Critics say it's the end of personal privacy as we know it. Advocates call it the tech advancement that will revolutionize security and means of identification.
What are the real implications of facial recognition?
In truth, it has yet to be determined. Each side poses valid arguments both for and against facial recognition. If you're interested in the pros and cons of facial recognition, check this out.
How does this budding - and controversial - technology fit into our daily lives?
Now that question we can answer. Let's dive into how facial recognition might enter our daily lives in the future.

Property management
Access control for enterprise
Corporations and universities spend millions each year on their campus security. Protecting their people, property, and other assets makes it a very worthy investment.
Facial recognition provides an alternative to ID badges, swipe key access, gate codes, and other means of access control.

Let's say you work in the R&D department at a large tech company. Currently, you have several layers of security when entering campus and even your office. With facial recognition, each access point (doors, gates, even office devices) instantly determines whether your profile has the proper permissions and records such activity.
Access control for residences
One of the biggest headaches for property managers and tenants is effective yet convenient access control. Apartment complexes and gated communities seem to have wildly inefficient means of controlling visitors.
Facial recognition allows for management to track and grant permanent access to tenants, temporary access to guests and contractors, and deny access to intruders.
Electronic passports and identification
E-passports and other forms of electronic identification is arguably the largest application for facial recognition.
The International Civil Aviation Organization (ICAO) is an agency of the United Nations. It exists as a proponent for international air navigation principles and focuses on development of international air travel.
ICAO prioritized facial recognition and other biometric technology as the primary standard for identification. In October 2006, the United States transitioned their non-visa agreements to an e-passport system that incorporated biometric features like facial recognition and fingerprints.

The Transportation Security Administration (TSA) plans to implement biometric-based domestic travel documents for US travel. Many countries in the EU plan to follow suit.
Criminal investigations
The FBI and other government agencies are utilizing facial recognition to track down fugitives and suspects on the run.
In June of 2018, authorities used facial recognition to identify the suspect of a shooting at an Annapolis newspaper since police struggled to identify the suspect using fingerprints alone.

The Next Generation Identification System (NGI) is a centralized database for mugshots. The software processes an image and returns a list of mugshots that might match the suspect.
It's important to note the privacy concerns associated with this application. Civil liberties groups have criticized that this technology may propagate invasions of privacy and racial profiling.
Self-service authentication
Rather than using a four digit PIN to authenticate an ATM withdrawal, imagine using face-scanning technology. In terms of security, facial recognition is much more effective and accurate for authenticating users.
To put things into context, consider your smart phone's security. Depending on its make and model, you probably use a combination of facial recognition, finger print scans, and a passcode to unlock the device. According to Apple, these are the odds of each authentication method getting hacked:
- 1 in 10,000 that someone guesses your four digit passcode
- 1 in 50,000 that someone else's fingerprint falsely unlocks your iPhone
- 1 in 1,000,000 that someone guesses your six digit passcode
- 1 in 1,000,000 that someone else's face falsely unlocks your iPhone
Information security
You can do anything on the internet:
- Book a trip to Thailand
- Buy a car
- File your taxes
- Get dinner delivered
- Invest your money
While e-commerce revolutionized our experiences as consumers, it also gives bad actors access to a plethora of your personal information. Facial recognition has the ability to accurately authenticate users for online transactions and to access confidential information.
Right now, most of this information is protected by users' passwords, which let's be honest, usually isn't all that secure.
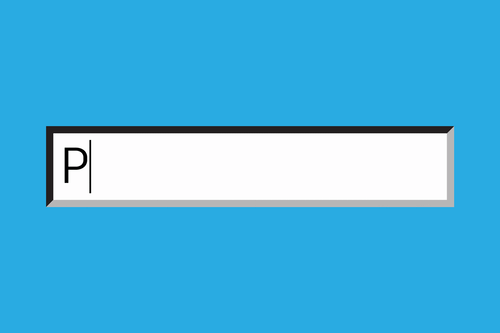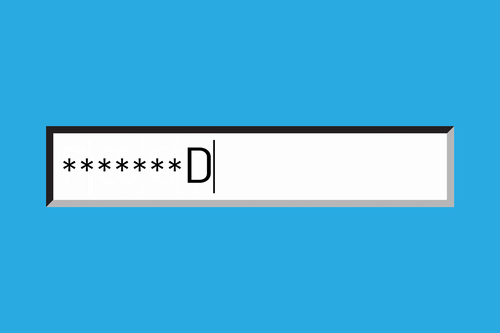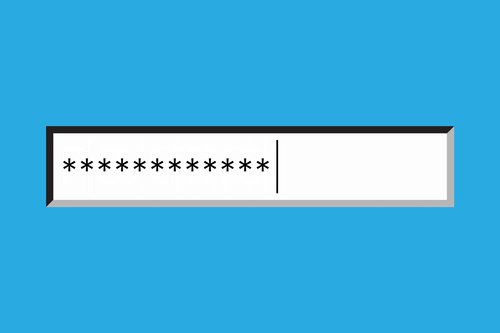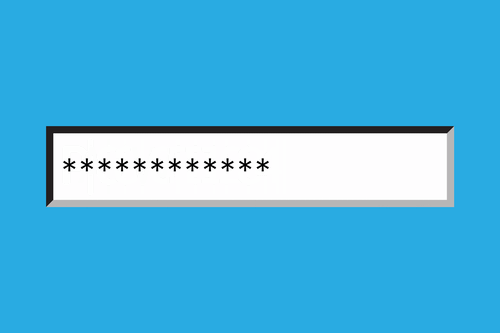
The wrap-up
With these applications alone, facial recognition has the ability to revolutionize security and authentication in our increasingly digital world. However, one must ask, at what cost? That is a debate that has yet to be settled.
As a society, we must consider how facial scans are stored and protected, how data is aggregated, and the origin of our data. It's our responsibility as citizens and consumers to hold organizations accountable for how they use and protect our data.




